Teazr, a “secure” dating app with privacy issues
I have to admit, one of my hobbies include watching API implementations and looking at the traffic flow between clients and backend-servers.
Teazr is the new kid on the block in the dating app scene, it is built by three danish guys, and they just recently received $250.000 in funding to take on the american market.
Their goal is to make dating more safe, so when you match with another user, you are forced into taking a picture of yourself, and you will get a picture in return from your match.
They claim that this process is unbreakable, and that this can’t be automated, and because of this their app is free of the robots that haunts their competitors like Tinder.
I wanted to see which kind of data that the app uses, and how it communicates with the backend. I used Charles Web Proxy to intercept the traffic, and the interface looks like this:
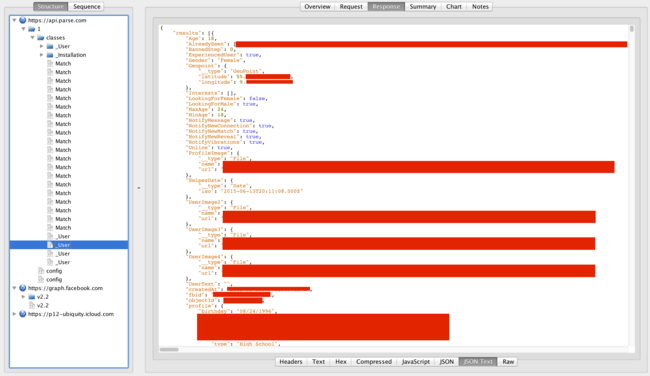
(I have since moved on to use mitmproxy...