Teazr, a “secure” dating app with privacy issues
I have to admit, one of my hobbies include watching API implementations and looking at the traffic flow between clients and backend-servers.
Teazr is the new kid on the block in the dating app scene, it is built by three danish guys, and they just recently received $250.000 in funding to take on the american market.
Their goal is to make dating more safe, so when you match with another user, you are forced into taking a picture of yourself, and you will get a picture in return from your match.
They claim that this process is unbreakable, and that this can’t be automated, and because of this their app is free of the robots that haunts their competitors like Tinder.
I wanted to see which kind of data that the app uses, and how it communicates with the backend. I used Charles Web Proxy to intercept the traffic, and the interface looks like this:
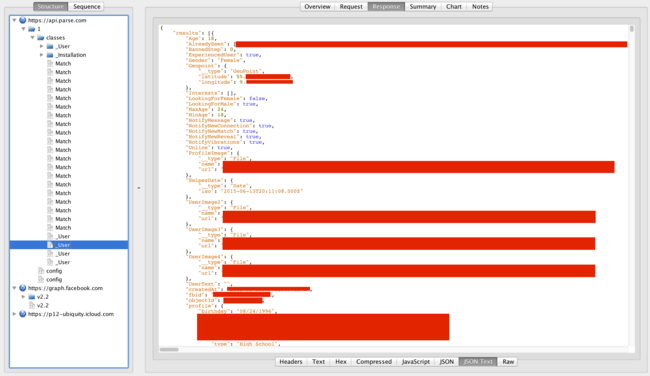
(I have since moved on to use mitmproxy for these kinds of activities)
If you look at the screenshot, you can see that the app connects to Parse.com, a hosted database and api in the cloud. And if you look even closer, you can see some of the data that the app is sending about a user includes their location, their EXACT location.
If you take the coordinates, and type it into Google Maps, you will find the exact house that the user are sitting in:
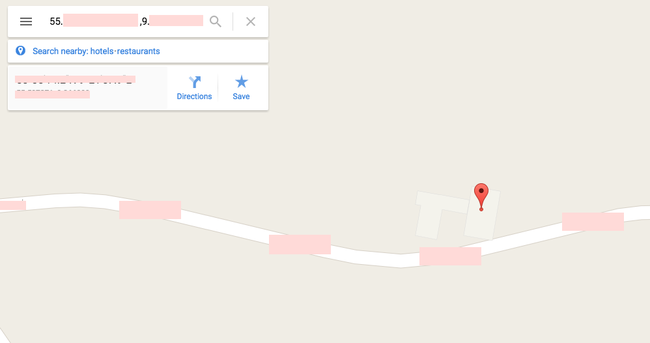
(My guess is that there is a comfortable couch just where the pin is)
Taking contact to Teazr and fixing the problem #
I immediately took contact to the CTO of Teazr, Simon Degn, and explained the problem to him. He was under the impression that using https and Parse everything was secure.
He promised to look into it, and fix it.
A month later when I looked back at the application, the problem have been fixed.